.
Cisco offers three solutions for eliminating STP. These comprise the stacking feature on 3750/2950 models, VSS on 6500s, and vPC on Nexus 5k/7k platforms. An important point to remember in comparison of these three methods is that in vPC, the control planes of the peer switches are separate, unlike Stacking/VSS where all switches are maintained by a single control plane.
Force10 Switches offer two solutions of this nature, which are discussed below.
-
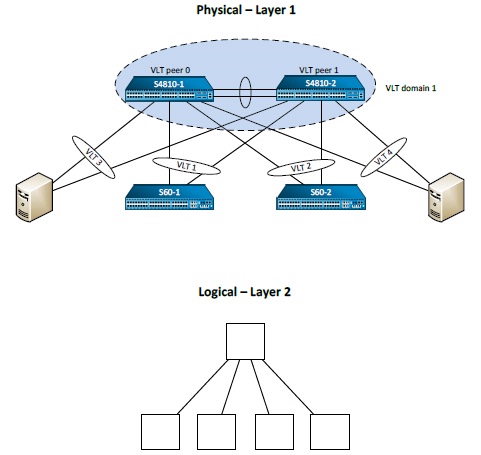
- Force10 switches, specifically S4810, offer a feature known as VLT (Virtual Link Trunking). VLT Is a Dual Active Control Plane implementation, of a Multi-System LAG. Thus, in operation, it is very similar to Cisco vPC.
-
-
- VLT is beneficial in environments where the downstream devices like access switches need to build port channels/Link Aggregation groups across two separate upstream switches. The downstream switches view the VLT peers as a single logical chassis, thus allowing the LAG group to be split across the two peers. The other benefit is that due to distinct control planes, it is possible to perform maintenance one switch at a time without taking the entire fabric down.
-
-
-
- For any switches with link to only one of the peers, they will continue to view the VLT peers as distinct switches. Spanning tree & the forwarding path will thus remain a consideration. Also, there is no unified management.
-
-
-
- However, the true benefit of the implementation is its simulation of a single logical chassis (like stacking, or Virtual chassis) for downstream switches, with the retention of distinct control planes on the actual switches. This in turn allows these switches to be taken down for maintenance one at a time, assuring there is at-least one of the pair available to switch traffic while the other one is attended to. Each switch continues to execute its own control plane protocols (STP, unicast routing etc.), unlike stacking.
-
-
-
- VLT, is limited to 2 peers. Stacking however, can accommodate up to 6 units (On S-Series) and more (~9) on N-Series.
-
-
-
- A sample of VLT configuration can be found in the following post: https://hasanmansur.com/2012/11/07/force10-s4810-vlt-quick-configuration-sample/
-
-
- The other option is the use of Stacking. Stacking maintains a single control plane, while the data plane obviously remains distinct on both switches. It provides the two switches as a single logical fabric, and the loss of one switch does not affect the forwarding of the data plane on the other switch. Thus, resilience is automatically accounted for. A Master failure, should result in the backup taking over the Master function. The current master continuously synchronizes its state with the backup during normal operation. The distributed forwarding tables are retained during the failover, as is the stack MAC address.
-
-
- The single logical chassis allows for easier maintenance as the stack is managed as one logical unit. Ergo, STP considerations too are minimal because of this very nature.
-
-
-
- Stacking (like VLT) uses QSFP 40G or 10G front end ports (in stack-groups of 4 ports), giving 40G aggregate bandwidth per port group (up to a maximum of 80G). VLT also makes use of QSFP or Stack groups. the following picture, from the Config Guide, gives a visual depiction of port groups.
-
-
-
- The downside is that the stack must be upgraded as a single unit. As it is a single logical chassis, the reboot required after any firmware upgrades would take down the entire fabric. A maintenance “lights out” window must be provisioned.
-
A few points to be mindful of when configuring VLT:
-
- STP, MSTP, and PVST are not supported. RSTP is a prerequisite. (Edit: 2017/02/05 – while this was correct when this blog post was committed, this is no longer the case. Owing to the many enhancements to VLT over the last few years, Per VLAN instances of STP can exist in conjunction with VLT. Always refer to the current user guides for the respective platforms, to confirm current capabilities and limitations)
- Configure the bridge priorities for deterministic behavior.
- Prefer static LAG between VLT peers and LACP towards hosts/switches.
- To become VLTi the port-channel must be in default mode (no switchport, no VLAN assigned).
- The backup link should be a different link than the VLTi and if possible following a diverse path. This could be the management interface IP address.
- You do not need to manually tag VLANs on the VLTi. The system does it by itself for any VLAN tagged on VLTs.
- Configure the primary VLT peer as the RSTP primary root device and configure the secondary VLT peer as the RSTP secondary root device.
.


nice explanation
Hi Hasan, We are recently migrating one of our DC from Cisco to Dell.. I was looking for the documentation part on the VLT’s.. This document helped me a lot. Thank you!!
Reblogged this on staniislaus and commented:
Force10 VLT Implementation
Thanks Hasan, your article was very helpful for planning the setup of our new S4840s
One significant gotcha is that when using a LAG in a stack you are able to configure the Seed Hash value to enable synchronous flows in the LAG. When using VLT Seeding the hash is not possible which means at no point can we accurately say which path data will flow. This is problematic when talking about security appliances and other session based devices. This is problematic when discussing I/O cards and how they are configured as well. Additionally, when deploying tiered VLT configuration the sessions become problematic through multiple tiers. OS10 does not support Stacking currently as well. So if you want to ensure session flows you are going to have to stick with OS9 at the moment.
This is valuable Insight, thanks. Hopefully would be of help/use to the readers.
Hello Hasan,
Firstly, thanks detail explation.
I have a question. I’ m useing 2 diffrent dell swtiches(S4112f – S4128f). I want to run vlt between these two devices. But the OS versions of the 2 devices are different from each other. Do I have a problem in this case?
S4112f – OS 10.4.2.0
S4128f – OS 10.4.3E
Kind Regards
Asalam Alaikum Hasan
Two VLT nodes with different revisions can be in production for short windows during upgrade/maintenance windows – It will work. However this discrepancy should not be sustained for long term in production. you should upgrade one of the nodes to the same revision as the other.
Thanks,